What is wrong with the fingerprint?
A while ago, we were developing an application for a fortune 500 company, which wanted to secure a mobile app containing vital data with the built-in fingerprint reader on iPhone and Android Devices.
Probably everybody is excited about the fingerprint tech because everyone owns a fingerprint, and each is unique. Also, these ideal security tokens conveniently stick with you everywhere you go. You don’t need to remember any passwords, use special USB devices, or generate keys stored on your smartphone. All you need to do is activate a sensor with your finger. Seconds later, you are in. Even though each fingertip is one of a kind, let’s see how fingerprint scanners manage to handle the security aspect of this authorization method.
Let’s take a sneak peek at how fingerprint readers work.
As I’ve already mentioned above, no two fingers are identical. You may have asked yourself this question before: do identical twins have the same fingerprint? The answer is no. Fingerprints are even more remarkable than our DNA, even though our genetic code is complex.
The chance of two people having the same fingerprints is 1 in 64 billion, which is less likely to happen than winning the lottery (potentially any lottery).
The reason for fingerprints’ distinctive characteristics is that they do not form genetically but physically. They appear even before we are born, in our mothers’ womb. They start being developed as “friction ridges” from the pressure on the fingers touching the surroundings while the baby is in the womb. Fingerprints fully develop three months before we are born.
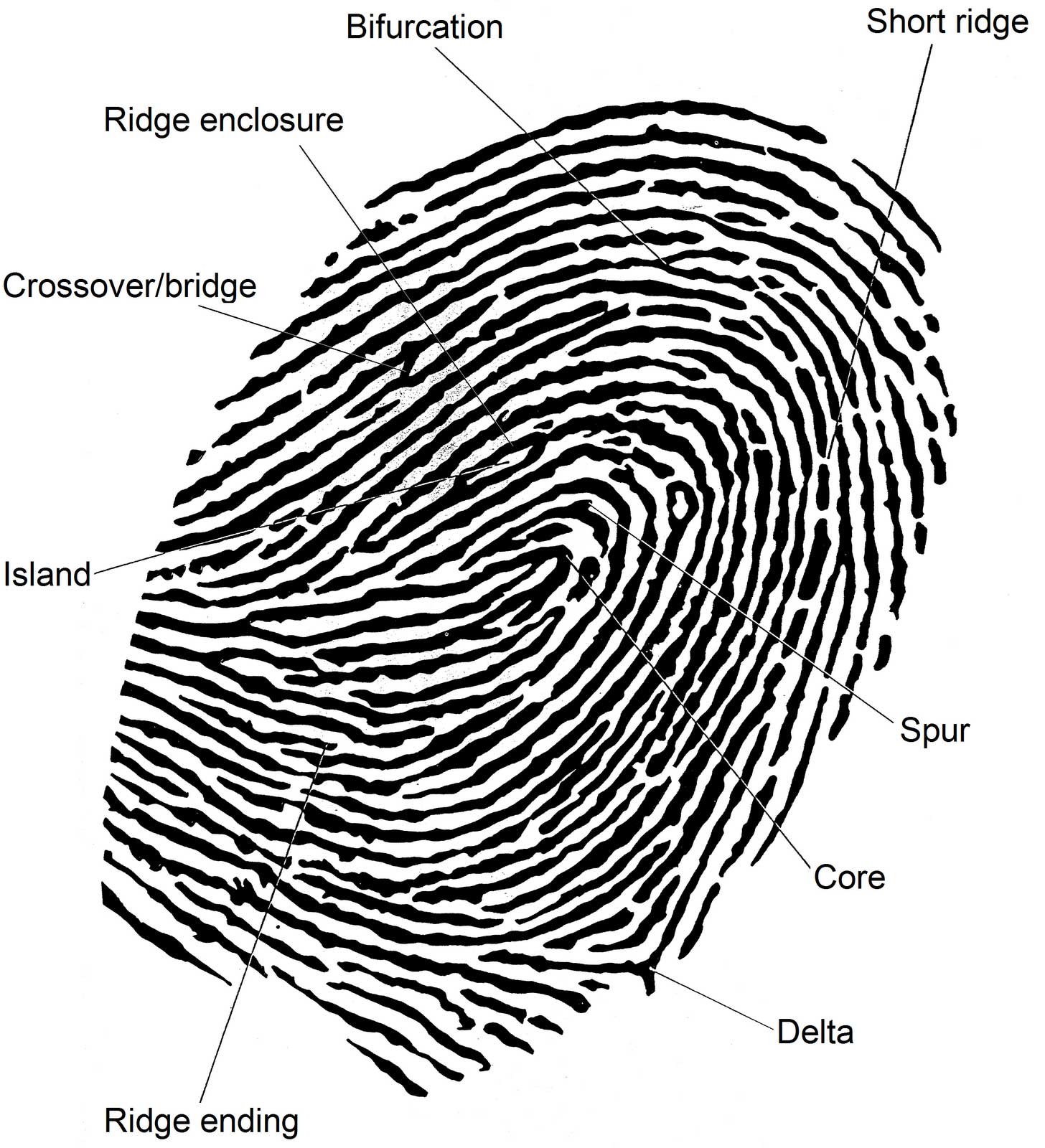
How does a Fingerprint reader work?
All of the ridges form patterns called loops, whorls, and arches. To distinguish one fingerprint from another and confirm the identity of the person behind them, some measurements are necessary. The measures taken into account are shape, size, number of lines in a pattern. From various characteristic points, we need to establish a grid of control points. As you can see in the above image, from all the measures, a certain point pattern arises. When this point pattern is compared with either another fingerprint or in the case of a fingerprint reader with a users’ fingerprint, the identity is confirmed – or not.

If fingerprints are unique – why aren’t they secure?
Everything seems perfect with your fingerprint as a security token, until you realize you leave instances of them everywhere. By saying everywhere, I mean they are everywhere. The FBI has them in a database, they are stored within your biometric passport and photo ID card, and you leave them whenever you touch something (except if you are a professional con artist wearing gloves all the time).
So, the pros of a fingerprint can easily be the cons at exactly the same time. Just imagine, everybody has access to your fingerprint, and the only thing you can’t do – is changing it.
Exploiting the fingerprint
The interesting part here is how to cheat the sensor of a fingerprint device. Back in 2002, a Japanese hacker demonstrated that he could do that with gummy bears. So basically, what you need is gelatin and some liquid silicone. However, technology has advanced now and new tech like 3D printers can model a glove with a copy of your fingerprints. As we’ve mentioned above, exploiting or misusing a fingerprint reader is not nuclear science and your prints are freely available on everything you touch. So, this is one of the most well-known cons of fingerprint tech – it’s easy to steal!
In conclusion, a fingerprint is convenient, but not a secure type of data protection. Therefore, we strongly recommend using it in combination with a second authentication factor.

